Shared Iptables Blacklist with Puppet
Created on 2010-11-08 by Yannick Vaucher
1 Introduction
In this document, is explained how we use puppet to share an iptables Blacklist. The aim is to be able to add an IP in that list and it will be automatically sent to all registered servers.
In order to protect us against some cyber attacks (sip frauds, sip or ssh brute force, etc) one thing to build is to deny access to intruders identified by their IP address.
2 Blacklist
The principle of making a list of bad IP that we want to deny is called Blacklist.
By sending the blacklist to our servers the firewalls can do their job.
2.1 Firewall - Iptables
On Unix systems, it is possible to set a firewall using iptables. By simple rules, it permits to allow or deny some to any kind of access on a server.
3 Puppet
This is a configuration manager that we use here to share our blacklist on all our servers.
To know more about puppet you can follow this link: Introduction on Puppet
3.1 Schema
Here is a little schema to describe the process.
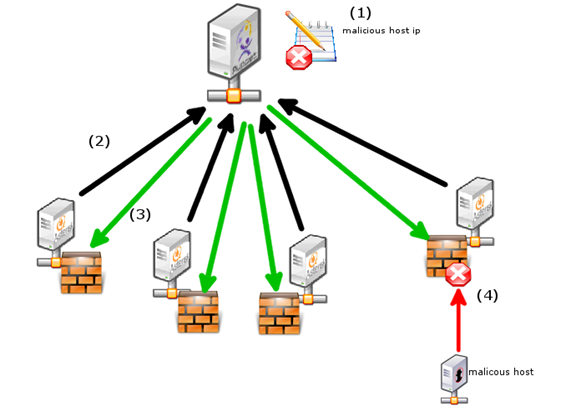
1) A list of ip addresses from unwanted hosts is defined on the puppet master server.
2) Each X time puppet client that are registered to the puppet master will ask if anything changed.
3) In case the blacklist was modified, the server gets the new blacklist. And will automatically update its firewall.
4) From now, the malicious host is blocked on all servers.
4 Puppet module iptables
4.1 Version 001
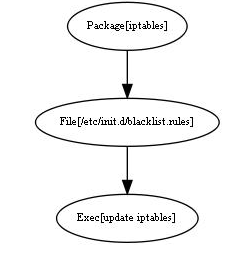
This little module is composed with 2 files: manifest/init.pp and files/blacklist.rules.
4.1.1 init.pp
What is needed for our blacklist to work is:
# /modules/iptables/init.pp
#
# Written on 110207 by
#
# This module is intended for debian only
#
# Copyright (c) Switzernet
#
class iptables {
package{ "iptables":
ensure => installed
}
file { "/etc/init.d/blacklist.rules":
owner => "root",
group => "root",
mode => 750,
source => "puppet:///iptables/blacklist.rules",
require => Package["iptables"],
notify => Exec["update iptables"]
}
exec { "update iptables":
refreshonly => true,
command => "sh /etc/init.d/blacklist.rules",
}
}
Iptables is restarted only if the file blacklist.rules is modified.
4.1.2 blacklist.rules
This file is the script that will update the firewall. It also include the list of ip to block.
#!/bin/bash
# Flush iptables
/sbin/iptables -F
# Blalisted IPs
# To add an IP add
# /sbin/iptables -A INPUT -s <ip_to_blacklist> -j DROP
/sbin/iptables -A INPUT -s 74.63.232.197 -j DROP
/sbin/iptables -A INPUT -s 91.206.226.210 -j DROP
/sbin/iptables -A INPUT -s 99.133.130.158 -j DROP
/sbin/iptables -A INPUT -s 188.165.227.176 -j DROP
exit 0
|
Version |
iptables v 001 |
|
File |
|
|
Size |
1290 B |
|
MD5 |
f9089acb36d0551414c1de41dd1d421a |
5 References
Introduction on Puppet
http://switzernet.com/3/public/110127-puppet-introduction/
puppet iptables module
http://missadmin.blogspot.com/2009/08/puppet-iptables-module.html
bobsh / puppet-iptables
https://github.com/bobsh/puppet-iptables
IPTables Module & Alternative
http://projects.puppetlabs.com/projects/puppet/wiki/Module_Iptables_Patterns
Blacklister une IP avec iptables
http://www.benjaminbaudouin.com/blacklister-une-ip-avec-iptables/
HOWTO: Building IPTables rules
http://wiki.vpslink.com/HOWTO:_Building_IPTables_rules
IPTablesHowTo
https://help.ubuntu.com/community/IptablesHowTo
How do I save iptables rules or settings?
http://www.cyberciti.biz/faq/how-do-i-save-iptables-rules-or-settings/