Fraudulent traffic to Slovenia mobiles
[]
The list of IP addresses and subnets for an immediate blacklisting
Emin Gabrielyan
Fraudulent traffic to Slovenia mobiles
1. Intensity of IP connections
2.1. On 2010-11-02 urgent request to block fraudulent destinations
4.2. Authorities of Slovenia and resolved frauds
6. MS Word formats particular to this document
6.1. Styles used in this document
6.3. Deleting the reference number bookmark before printing
6.4. Conventions on maintaining versions of a web document when uploading via ftp
This document shows the retrieval of the IP addresses appearing in syslog files [101] [102] [103] of servers hacked in October 2010 [104] [105] [106] [107]. The retrieved data is sampled over 1-minute intervals. All IP addresses appearing in an interval are recorder with the numbers of their occurrences. The phone numbers to black list appear in a separate document [108] [109]. The updates are available in section 2. Since the first publication another black list is emerged (see section 2.1).
The IP addresses as well as the phone numbers are provided for black listing and prevention of further frauds. This is also a call to all authorities in all concerned countries.
1. Intensity of IP connections
The following chart shows the number of IP records per hour estimated to be the source of fraudulent transactions.
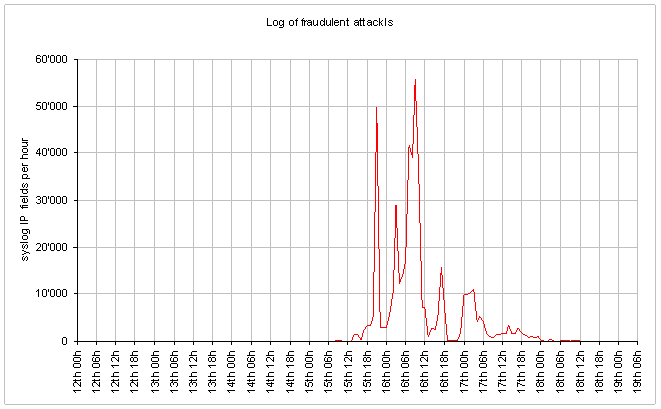
[xls]
The same chart is shown in the logarithmical scale:
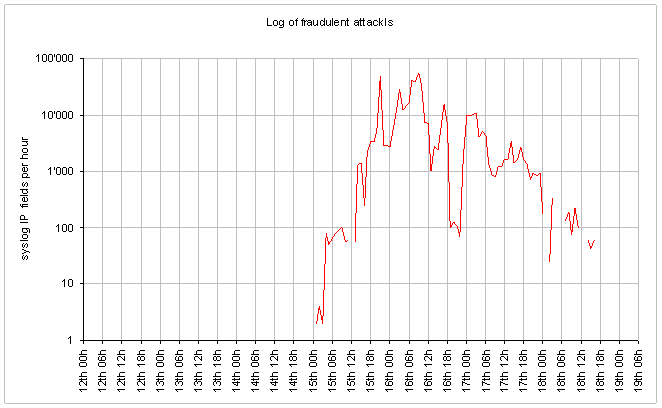
[xls]
1.1. Statistics per subnet
The top subnets retrieved from syslog during the fraud are shown in the table below. The geo location of IP addresses can be estimated via one of the 4 links accompanying the IP address subnet. If the IP address is still not found, try the 5th solution ipligence.com [110] by typing in the three octets in question followed by “1” for the 4th one.
|
The first 3 octets of the IP Address |
Number of occurrences |
ip-address-lookup-v4.com |
geoiptool.com |
ipgetinfo.com |
hostip.info |
|
188.161.135. |
26540 |
||||
|
188.161.239. |
22329 |
||||
|
188.161.237. |
20321 |
||||
|
188.161.134. |
13342 |
||||
|
188.161.231. |
9788 |
||||
|
188.161.240. |
8699 |
||||
|
188.161.136. |
8628 |
||||
|
188.161.234. |
8262 |
||||
|
188.161.236. |
7931 |
||||
|
188.161.235. |
7637 |
||||
|
188.161.147. |
7582 |
||||
|
188.161.229. |
6545 |
||||
|
188.161.230. |
5739 |
||||
|
41.206.155. |
5300 |
||||
|
95.35.232. |
4946 |
||||
|
109.253.235. |
3846 |
||||
|
188.161.238. |
3820 |
||||
|
41.206.148. |
3448 |
||||
|
188.161.228. |
2794 |
||||
|
188.161.144. |
2242 |
||||
|
188.161.133. |
2148 |
||||
|
41.206.158. |
1894 |
||||
|
188.161.140. |
1888 |
||||
|
41.206.153. |
1846 |
||||
|
109.253.170. |
1632 |
||||
|
188.161.220. |
1562 |
||||
|
188.161.141. |
1440 |
||||
|
202.60.88. |
808 |
||||
|
109.253.86. |
756 |
||||
|
41.206.151. |
584 |
||||
|
41.206.149. |
486 |
||||
|
188.161.233. |
450 |
||||
|
188.161.232. |
360 |
||||
|
41.206.156. |
326 |
||||
|
188.161.137. |
318 |
||||
|
91.121.40. |
308 |
||||
|
188.161.142. |
248 |
||||
|
91.121.39. |
244 |
||||
|
188.161.227. |
232 |
||||
|
188.161.139. |
230 |
||||
|
74.115.6. |
206 |
||||
|
188.161.146. |
198 |
||||
|
188.161.143. |
172 |
||||
|
188.161.138. |
112 |
||||
|
91.121.49. |
110 |
||||
|
91.212.226. |
104 |
||||
|
91.121.63. |
100 |
||||
|
188.165.0. |
74 |
||||
|
188.161.241. |
66 |
||||
|
41.206.150. |
48 |
||||
|
76.191.104. |
48 |
[xls]
2. Updates
2.1. On 2010-11-02 urgent request to block fraudulent destinations
Due to escalating fraudulent activity an Australian operator asks all peers to block the following numbers for its roaming subscribers.
|
Fraudulent destinations to block |
|
248985311 |
|
248985312 |
|
248985313 |
|
248985314 |
|
248985315 |
|
248985316 |
|
248985317 |
|
261200201048 |
|
261200201049 |
|
261200201130 |
|
261200201131 |
|
261200220460 |
|
37091006844 |
|
37091006845 |
|
37091006846 |
|
37091006847 |
|
881842011124 |
|
881935211566 |
|
881935211567 |
The IP address 202.60.88.238 that frequently appeared in syslogs of the hacked servers (see the log of accesses [xls] 1.19 MB) is in Australia:
8 14 ms 13 ms 13 ms 10gigabitethernet1-4.core1.zrh1.he.net [91.206.52.170]
9 19 ms 19 ms 21 ms 10gigabitethernet3-2.core1.fra1.he.net [72.52.92.229]
10 35 ms 36 ms 35 ms 10gigabitethernet1-2.core1.par1.he.net [72.52.92.89]
11 35 ms 36 ms 36 ms 10gigabitethernet1-3.core1.lon1.he.net [72.52.92.33]
12 104 ms 104 ms 103 ms 10gigabitethernet2-3.core1.nyc4.he.net [72.52.92.77]
13 116 ms 110 ms 115 ms 10gigabitethernet2-3.core1.ash1.he.net [72.52.92.86]
14 178 ms 185 ms 178 ms 10gigabitethernet1-4.core1.pao1.he.net [72.52.92.29]
15 218 ms 178 ms 178 ms e3-networks.gigabitethernet6-10.core1.pao1.he.net [64.62.134.178]
16 180 ms 180 ms 180 ms ip-73.199.31.114.VOCUS.net.au [114.31.199.73]
17 353 ms 353 ms 353 ms ge-0-0-2-10.bdr01.sjc01.ca.VOCUS.net.au [114.31.199.60]
18 354 ms 353 ms 353 ms ge-0-1-0-135.cor02.syd03.nsw.VOCUS.net.au [114.31.192.72]
19 353 ms 353 ms 364 ms ge-0-0-0.bdr01.bne02.qld.VOCUS.net.au [114.31.192.85]
20 353 ms 353 ms 375 ms ge-0-0-3.bdr01.bne01.qld.VOCUS.net.au [114.31.194.112]
21 382 ms 353 ms 353 ms as24238.bne01.qld.VOCUS.net.au [114.31.195.38]
22 354 ms 356 ms 353 ms 202.60.88.238
The machine replies to ping and is apparently also a SIP server as it accepts connections to the port 5060:
$ telnet 202.60.88.238 5060
Trying 202.60.88.238...
Connected to 202.60.88.238.
Escape character is '^]'.
telnet> q
Connection closed.
3. Description of the script
The script scans all syslog files and generates a CSV file, with the time (an interval of 60 seconds), IP address, and the number of its occurrences (within the current interval).
$ for f in 1010??-syslog.txt; do echo [$f]; grep "ser\[" $f | perl -ne 'while(<>){/^([a-z]+ \d+ \d+:\d+):\d+ /i; $t=$1; while(s/(?<!\d)((?:\d+\.){3}\d+)(?!\d)/_/){$n{$t.",".$1}++}} foreach (keys %n) {print $_.",".$n{$_}."\r\n"}' | sort > `basename $f .txt`.csv; done
[101013-syslog.txt]
[101014-syslog.txt]
[101015-syslog.txt]
[101016-syslog.txt]
[101017-syslog.txt]
[101018-syslog.txt]
[101019-syslog.txt]
The Perl script checks each line of the syslog file and captures all IP addresses appearing in the line. Whenever an IP address is found in the line, it is voided (by a dummy replacement) in order to check the rest of the line for other occurrences of an IP address:
while(s/(?<!\d)((?:\d+\.){3}\d+)(?!\d)/_/){$n{$t.",".$1}++}}
In the expression we use a zero-width negative look-behind assertion “(?<!pattern)” and a zero-width negative look-ahead assertion “(?!pattern)”.
The script generates a table of the following format. For more information, the time and data provided in this table must be correlated with the time and data of the CDR file found from the syslog files [111].
|
Date and Time |
IP address |
Count |
|
2010-10-12 13:51 |
192.168.1.9 |
2 |
|
2010-10-12 18:07 |
192.168.1.9 |
2 |
|
2010-10-13 00:32 |
192.168.1.9 |
2 |
|
2010-10-13 06:15 |
192.168.1.9 |
2 |
|
2010-10-13 11:22 |
192.168.1.9 |
2 |
|
2010-10-13 13:13 |
188.161.231.133 |
2 |
|
2010-10-13 13:14 |
192.168.1.9 |
2 |
|
2010-10-13 13:45 |
192.168.1.9 |
2 |
|
2010-10-14 12:44 |
192.168.1.9 |
2 |
|
2010-10-15 01:59 |
188.161.233.159 |
2 |
|
2010-10-15 02:58 |
188.161.233.159 |
2 |
|
2010-10-15 02:59 |
188.161.233.159 |
2 |
|
2010-10-15 03:37 |
192.168.1.9 |
2 |
|
2010-10-15 04:13 |
188.161.233.159 |
2 |
|
2010-10-15 04:14 |
188.161.233.159 |
8 |
|
2010-10-15 04:16 |
188.161.233.159 |
4 |
|
2010-10-15 04:18 |
188.161.233.159 |
2 |
|
2010-10-15 04:33 |
192.168.1.6 |
6 |
|
2010-10-15 04:34 |
192.168.1.6 |
2 |
|
2010-10-15 04:35 |
188.161.233.159 |
2 |
(truncated)
[xls]
4. References
4.1. Fraud reports
Retrieving the IP addresses by time (this page) [112]:
http://switzernet.com/3/public/101029-fraud-slovenia/
Retrieving the CDR from syslogs [113]:
http://switzernet.com/3/public/101028-fraud-slovenia/
http://switzernet.com/public/060801-web/news_detail.php?id=167
http://switzernet.com/public/060801-web/news_detail.php?id=166
Communication to authorities [116] [117]:
http://switzernet.com/3/folders/101018-fraud-slovenia/ (login: fraud)
http://www.fedpol.admin.ch/content/fedpol/fr/misc/conform.html
Fraud with calls to Lithuania [118]:
http://switzernet.com/3/folders/100702-lithuania-fraud/ (login: police)
4.2. Authorities of Slovenia and resolved frauds
2010-07-28 Hacker Suspected in Huge Scam Arrested in Slovenia [voanews.com] [cached]
2010-07-29 Slovenian arrested in global cyber scam case [allbusiness.com] [cached]
2009-06-08 Télécommunications: la Commission autorise l’autorité réglementaire slovène à continuer de réguler le marché de la téléphonie mobile [europa.eu] [cached]
4.3. Projects
ACD quality routing [119] [120] [121] [122] [123] [124] [125] [126] [127]:
http://switzernet.com/public/091020-acd-routing/
http://www.unappel.ch/2/public/091020-acd-routing/
http://unappel.ch/public/091020-acd-routing/
http://intarnet.com/2/public/091020-acd-routing/
http://parinternet.ch/2/public/091020-acd-routing/
http://switzernet.com/public/091029-ACDstat/
http://unappel.ch/public/091029-ACDstat/
http://switzernet.com/public/091217-doc-acd-routing/
http://en.wikipedia.org/wiki/Least-cost_routing
Emergency numbers [128]:
http://unappel.ch/folders/101004-emergency-calls-planning/ (login: ofcom)
4.4. Other references
Kamalio/OpenSER SIP server/router [129] [130] [131]:
Perl regular expressions [132] [133]:
http://switzernet.com/3/public/101024-regex/
http://perldoc.perl.org/perlre.html
References on syslog file format [134] [135] [136]:
http://www.facetcorp.com/tnotes/facetwin/tn_syslog.html
http://lists.rtpproxy.org/pipermail/users/2009-May.txt
IP Address Geo location [137] [138] [139] [140] [141]:
http://www.ipligence.com/geolocation
http://ip-address-lookup-v4.com/
5. Files
Syslog file of 2010-10-13 [zip] (15.3 KB)
Syslog file of 2010-10-14 [zip] (613 KB)
Syslog file of 2010-10-15 [zip] (798 KB)
Syslog file of 2010-10-16 [zip] (8.19 MB)
Syslog file of 2010-10-17 [zip] (8.35 MB)
Syslog file of 2010-10-18 [zip] (3.31 MB)
Syslog file of 2010-10-19 [zip] (49.5 KB)
CSV files of IP addresses [zip] (83.3 KB)
The merged CSV file [csv] (640 KB)
The Excel file of IP addresses and stats [xls] (1.19 MB)
The Excel file of all IP addresses [xls] (1.55 MB)
Log of the command line scripts [zip]
A. Krenker, bi-ANN for mobile phone fraud detection, 2009 [pdf]
6. MS Word formats particular to this document
6.1. Styles used in this document
The following image shows the styles used in this document. Do not add new styles when editing and updating this document.
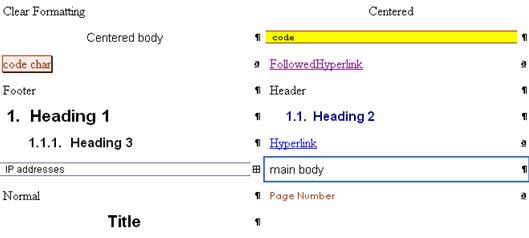
6.2. Numbering of references
Microsoft field codes are used for the square bracket surrounded auto incremental reference numbers of this document. In order to see the code, first remove the hyperlink (Ctrl-K), and then chose toggle field codes from the right-click pop-up menu.
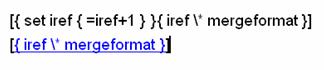
To add a new reference you need to copy any of the other references and change only the hyperlink. You do not need to care about the numbering as they are all updated by selecting the entire document and choosing [Update Field] in the right-click pop up menu.
6.3. Deleting the reference number bookmark before printing
Before printing the document, update all fields (as explained in section 5.2) and delete the “iref” bookmark (Alt-I-K). Otherwise, all references will appear under the same number.
6.4. Conventions on maintaining versions of a web document when uploading via ftp
Your main page must be written in a numbered index<N>.doc file, where <N> is the version number of the document that starts from 1 and auto increments. The document must be saved in index<N>.htm file. Use the “Web page, Filtered (*.htm; *.html)” type when saving. The saving will create an automatically generated folder index<N>_files together with the index<N>.htm file. Every time a new version is released, the index.htm file must be deleted, and the last index<N>.htm file must be copied and renamed into the new index.htm file. The index.htm file must be the copy of the last index<N>.htm file all the time. The index.htm file can be erased at any time when a new version is released. You must not have index.doc file. The folder index_files (corresponding to index.htm file) must be deleted (if created at the copy time) as the index.htm file refers anyway to the files located in the folder index<N>_files. At every update you must add in the header of the document your name and under the update date (in YYYY-MM-DD format) a link to the current version of index<N>.htm file (and not to index.htm). These links are useful for backtracking to previous versions.
Your various data files accompanying your document (not the files generated automatically when saving in HTML format) must be located in data<M> folder, where <M> is another incrementing counter and is not necessarily equal to <N>. Do not hesitate to create your own data<M> folder every time theme it can be useful rather than to add your pieces in the already existing data<M> folder of the previous author.
* * *
![]()
Copyright © 2010 by Switzernet